Adversarial Machine Learning: Techniques, Risks, and Applications
Jun 19, 2025Security concerns are rising with the incessant growth experienced in the field of AI and ML, as the models are increasingly becoming sophisticated. One of the paramount areas that have captured the attention of professionals and researchers in this field is Adversarial Machine Learning (AML). It refers to a kind of machine learning attack where hackers with malicious intentions manipulate inputs to deceive the model into making erroneous predictions or classifications.
In this article, we will explore Adversarial Machine Learning, its working, risks and applications. This article also provides insights into the growing need for enhanced security in machine learning models.
What is Adversarial Machine Learning?
Adversarial Machine Learning is designed in a way that it deceives the models by providing misleading inputs, which are also known as adversarial examples, to induce incorrect inferences. These attacks modify data in ways that appear harmless to humans but perplex machine learning models, undermining their accuracy. Adversarial attacks can cause significant errors in applications like image classification, speech recognition, and cybersecurity. Take, for instance, the alteration of a stop sign image can misinform an autonomous vehicle, which can lead to wrong interpretation and potentially cause accidents. The consequences of adversarial attacks are profound and far-reaching in critical systems within healthcare, finance, and autonomous transportation, as ML is deeply integrated in these sectors and is being widely used nowadays.
Origins of Adversarial Machine Learning
Adversarial Machine Learning started as early as the 2000s, when scientists realized that ML algorithms, particularly neural networks, were manipulable by minute variations in input data.
One of the first key papers arrived in 2004, when Dalvi et al. demonstrated how spam filters could be manipulated by making minor modifications to spam emails, without changing their intent. This was one of the first real-world demonstrations of adversarial attacks. However, the field only came into prominence after a landmark work by Szegedy et al. in 2013, where they showed that the addition of small, imperceptible noise to an image might lead a deep neural network to misclassify it entirely. This ignited the contemporary trend in adversarial ML.
Major Milestones in Adversarial Research
2013: Szegedy et al. propose the concept of adversarial examples in deep learning. It was an eye-opener to the AI community.
2014: Goodfellow et al. introduce the Fast Gradient Sign Method (FGSM), a simple and efficient way to produce adversarial examples. This facilitated attacks to be easier to reproduce.
2015–2017: Scientists delve into transferability, where adversarial examples generated for one model deceive other models as well. This brings into the limelight the deep weaknesses of most AI systems.
2018 and beyond: Adversarial attacks expand to black-box models (where attackers are unaware of the model's internal details), real-world objects (such as road signs) and even physical environments, increasing the risk factor.
Present Time: Adversarial ML is currently a central topic in AI security, with mounting interest in defenses such as adversarial training, robust optimization and certified defenses.
How do Adversarial Machine Learning attacks work?
Cyber intruders are behind adversarial machine learning attacks as they are the ones who manipulate the input data or the model’s internal mechanisms to mislead the system. The attackers aim to degrade the performance of the model by introducing subtle changes to the input data. This reduces the model's performance to the extent that it misclassifies or gives faulty predictions. These attacks can work on various machine learning models, including deep learning networks, Support Vector Machines (SVMs), and linear regression models.
Adversarial attacks can be classified into three major categories: poisoning attacks, evasion attacks, and model extraction attacks.
1. Poisoning attacks
This type of adversarial attack happens when the attackers contaminate training data or its labels. This results in incorrect predictions by the model. Since malicious data is continuously fed into the system, Poisoning Attacks can degrade the performance over time.
2. Evasion attacks
Evasion attacks manipulate input data during deployment to bypass detection, like altering malware to avoid detection.
3. Model extraction attacks
These attacks involve probing a black-box system to steal its model or training data. It compromises proprietary or sensitive models for malicious use or personal gain, such as financial, healthcare, or autonomous vehicle systems.
Evolution of Attack Methods
In the early days, adversarial attacks were primarily straightforward and white-box, i.e., attackers required complete model access. They used to introduce minor noise to deceive the system. Present times have seen attacks evolve significantly:
Black-box attacks: These function without having knowledge about the model's specifics, making them more real-world relevant.
Physical-world attacks: This comprises modifications of items such as road signs or glasses that deceive facial recognition systems.
Adaptive attacks: They are engineered to circumvent certain defense measures, showcasing that even secured systems are not immune.
The transition from mere digital stunts to sophisticated real-world manipulation demonstrates that adversarial attacks are on the rise and becoming increasingly difficult to prevent
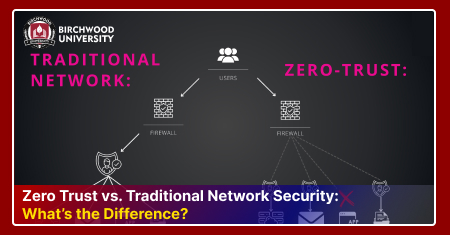
White-Box vs. Black-Box Attacks in Adversarial Machine Learning
A comparative analysis:
White-Box Attacks provide the attacker with full knowledge of the machine learning model. This allows for exact construction of adversarial examples with methods like:
Fast Gradient Sign Method (FGSM)
Projected Gradient Descent (PGD)
Example: A scientist checking a face recognition model is able to access its neural network weights. They use PGD to subtly alter a photo of one individual so that it would be misclassified as another, without any visual changes apparent to human eyes.
Black-Box Attacks are when the attacker has access only to the outputs of the model. They normally rely upon:
Query-based strategies (such as Zeroth Order Optimization)
Transferability (employing a substitute model to create transferable adversarial examples)
Example: An attacker is attacking an online object detection API. They produce thousands of queries, harvest output labels and train a substitute model. Then they produce adversarial examples that effectively deceive the original black-box model.
Impact on Defense Strategies
For white-box attacks, defense needs to target internal robustness—like injecting adversarial examples into training and using gradient masking or regularization.
For black-box attacks, restricting access is most important. This encompasses rate limiting, output restrictions or flagging suspicious patterns in probe indicators that suggest automated probing.
What is an Adversarial Example?
The data input that has been manipulated with the intention to deceive a machine learning model is called an Adversarial Example. These adversarial examples are almost indistinguishable from legitimate inputs to human observers; however, they are designed to influence the model's prediction accuracy. For example, a human would still recognize a slightly modified image of a dog but it may be classified by a deep learning model as a cat.
There are various techniques by which adversarial examples can be generated. The major challenge in adversarial machine learning lies in the ability to produce minimal perturbations to inputs, to make sure they go unnoticed by users but still distort machine learning outputs successfully.
Popular Adversarial AI attack methods
There are several techniques used to generate adversarial examples. These include modification of pixels, features, and other data aspects so that machine learning models are fooled. Some popular adversarial AI attack techniques are as follows:
Limited-memory BFGS (L-BFGS): This technique is a type of gradient-based optimization that works by minimizing perturbations of inputs. L-BFGS is computationally expensive and usually not used for real-time usage.
FGSM: The simplest and fastest method that applies the perturbation to all features to mislead the model, though less accurate.
JSMA: Uses key features to apply perturbation for higher efficiency, but is computationally heavy.
Deepfool attack: Finds minimal perturbations to change a model's predicted class, efficient with fewer modifications.
C&W: An optimization-based attack to craft adversarial examples, which bypasses defenses but is expensive in terms of computations.
Generative Adversarial Networks (GANs): Two neural networks compete to generate and identify adversarial examples, creating sophisticated attacks.
Zeroth-Order optimization attack (ZOO): A black-box attack that estimates gradients through altered inputs, effective without knowledge of the model.
Adversarial Attack Testing Tools and Frameworks
Popular Libraries CleverHans: TensorFlow library for designing and defending against adversarial examples. Foolbox: PyTorch and JAX-friendly, supports a variety of attack approaches. IBM Adversarial Robustness Toolbox (ART): Provides attack, defense and evaluation tools across several frameworks. Benchmarking Tools & Datasets RobustBench: Robustness benchmark leaderboards. ImageNet-A / CIFAR-10: Standard datasets to test adversarial robustness. AutoAttack: Comprehensive evaluation suite with multiple strong attacks. The risks of adversarial machine learning are enormous and varied. As machine learning is increasingly penetrating critical sectors such as healthcare, finance, and autonomous vehicles, the impact of adversarial attacks becomes even more alarming. Some of the key risks include: Security vulnerabilities: Attacks through adversarial approaches can be used to compromise trust in machine learning systems, especially when implemented in critical infrastructures such as cybersecurity, facial recognition, or financial modeling. Loss of model performance: The models under adversarial attacks tend to drop accuracy significantly, thus making incorrect predictions and erroneous decisions. Financial and reputational damage: Machine learning models targeted by attackers result in a significant financial loss and reputation damage for the organization. Compliance: Governments and regulatory bodies are concerned with the ethical implications of adversarial attacks, especially in areas like autonomous vehicles and surveillance. Researchers in 2020 showed that adversarial stickers applied to road signs could trick Tesla's Autopilot system. For instance, minor variations in a stop sign would make the vehicle read it as a speed limit sign. This raised concerns about real-world safety risks in self-driving. Outcome & Lessons: Tesla and other automakers started testing vision systems in adversarial scenarios. Increased emphasis on sensor fusion—integrating data from cameras, radar and LiDAR to improve decision-making. Tesla and its partners focused on strong training data and AI verification across different real-world conditions. Impact on AI Strategy: Reinforced the need for adversarial robustness in computer vision models. Accelerated investment in multi-modal AI models for safety-critical tasks. Google researchers have been leaders in adversarial machine learning research, especially via the TensorFlow and JAX ecosystems. Google released a number of results in 2019 about how minimal adversarial perturbations can mislead high-accuracy image models. Outcome & Lessons: Google brought tools such as TensorFlow Privacy and CleverHans (an open-source library for adversarial attacks) to assist developers in creating more secure models. Internal teams implemented strong training methods and started publishing benchmarks against adversarial vulnerability. Impact on AI Strategy: Strengthened emphasis on privacy, robustness and explainability. Integrated secure-by-design principles in Google Cloud AI products. Microsoft has taken a proactive approach by releasing the Adversarial ML Threat Matrix, a tool built in partnership with MITRE. It charts various adversarial attack types and countermeasures—similar to threat models in cyber security. Outcome & Lessons: Microsoft Azure integrated security for AI workloads, such as anomaly detection and model monitoring. Organizations were urged to consider machine learning as a fresh attack surface, correlating AI security with current IT security processes. Impact on AI Strategy: Encouraged a zero-trust culture for AI models. Influenced Microsoft's Responsible AI practices development, such as resilience and reliability. A number of healthcare AI systems, particularly those employing image-based diagnoses (e.g., identifying tumors on MRI scans), were found to be susceptible to adversarial inputs. A 2018 study demonstrated how slight alterations in medical images led diagnostic models to produce erroneous predictions. Outcome & Takeaways: Hospitals and medical research institutions started subjecting AI models to adversarial stress tests. Review protocols were put in place by organizations to integrate human experience with AI suggestions. Impact on AI Strategy: Greater need for certified AI systems in medicine. There will be more collaborations with universities and security researchers to validate model robustness prior to clinical deployment. Adversarial robustness refers to a model's capability to provide accurate predictions despite inputs being slightly tampered with to mislead it. Robust models are better in actual or adversarial environments. Adversarial Training Gradient Masking Input Preprocessing Ensemble Methods Certified Defenses Developing robust ML models involves striking a balance between security and accuracy, particularly in key uses such as finance, healthcare and self-driving systems. Adversarial machine learning is an extremely important research field notwithstanding its risks. This has some very crucial applications, including the following: Security systems: Adversarial machine learning techniques help test and build more robust security systems, such as spam filters, intrusion detection systems, and so on. Model reliability: Understanding adversarial attacks contributes to more robust and resilient machine learning models that can work with unexpected inputs. AI fairness and bias: Harnessing adversarial techniques will help test the machine learning models for their fairness and biases so that the algorithms work fairly for diverse populations. Self-driving vehicles: The research in adversarial attacks is helpful in making perception and decision-making systems of autonomous vehicles more secure. Adversarial AI will become more sophisticated. Attacks will increasingly focus on real-world applications including autonomous vehicles, biometric systems, and language models. In the meantime, regulatory pressure will see industries increasingly implement robust-by-design standards and adversarial testing as part of routine AI validation. Quantum Computing potentially would accelerate adversarial example generation by using search optimization in high-dimensional input spaces. Alternatively, it might fuel more powerful defenses in the form of quantum-secure models. Neuromorphic AI, duplicating the human brain's structure, potentially would be inherently resistant to some adversarial attacks—but its complexity creates new, unknown vulnerabilities. The arms race between attackers and defenders will escalate: Attackers will employ generative AI and automated toolkits to create undetectable adversarial inputs. Defenders will be dependent on AI-native security stacks, adversarial training pipelines and AI-based monitoring systems. This arms race will stimulate innovation in adversarial risk management and define the next generation of reliable AI systems. Adversarial Machine learning brings significant threats to the model's integrity while offering opportunities for strengthening robustness, security, and fairness. Along with a continuous growth of deceptive attacks, researchers and organizations must advance in line with defense approaches, such as adversarial training and resilient optimization.Risks of Adversarial Machine Learning
Case Studies: Companies Battling Adversarial Threats
Tesla: Adversarial Attacks on Self-Driving Systems
Google: Securing Image Classification and Cloud AI
Microsoft: Enterprise-Grade AI Defense Tools
Healthcare Institutions: Protecting Medical AI Systems
Adversarial Robustness and Resilient ML Models
What Is Adversarial Robustness?
Techniques to Improve Resilience
Incorporates adversarial examples into training to boost resistance.
E.g., FGSM, PGD-based training.
Obscures model gradients to hinder attacks, though may offer only temporary protection.
Uses image transformations or noise reduction to clean inputs before processing.
Combines multiple models to reduce the success rate of targeted attacks.
Offers mathematical assurances of robustness within given bounds.
E.g., randomized smoothing, interval bound propagation.Trade-offs: Accuracy vs. Security
Applications of Adversarial Machine Learning
Future Trends in Adversarial AI
Predictions for 2025 and Beyond
Emerging Technologies: Quantum & Neuromorphic AI
The Ongoing Arms Race
Conclusion