Zero Trust vs. Traditional Network Security: What’s the Difference?
Jun 23, 2025The threat landscape today has evolved into a highly sophisticated level, requiring enterprises to shift from traditional network security to the Zero Trust methods. However, there is an increasing debate centred around zero trust versus traditional methods. This blog is a comprehensive discussion about the difference between these two security parameters. Let us explore the key features that differentiate one architecture from the other in securing the digital landscape today.
To understand the key difference of these two security models, let us discuss each of them separately.
Understanding Traditional Network Security
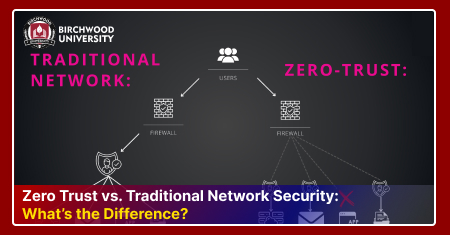
The Traditional model is also referred to as 'castle-and-moat' approach. This method keeps external threats and secures the network by leveraging perimeter protections like firewalls, IDS (Intrusion Detection System) and other security measures. Similar to being inside a castle walls, once entering a network, the users and systems are considered safe and are trusted by default. Users are therefore given unrestricted access to information or resources, facilitating a false sense of security. This model, however, lacks when it comes to addressing insider threats and cyberattacker's lateral movements once they break into the security/perimeter defences. This approach modelled on the idea that accessing from outside the network is difficult, hence all the resources inside are safe by default.
The Traditional perimeter security leverages several key components. Some of them are:
Firewalls: It is a software or hardware solution that checks and filters the network traffic and allows only a certain type to get through the traffic
IDS (Intrusion Detection System): This perimeter monitors activities on the network and keep check of anomalies and suspicious behaviour. It raises alarm and alerts when it detects unusual activity.
VPN (Virtual Private Network):VPN makes use of encryption for securing data transmitted from the organization's internal network to the Internet.
In the traditional network security methods, these components provide a secure perimeter to an organization's network. Although it offers a certain level of protection, it often lacks to provide an ideal security solution.
Understanding Zero Trust Security Model
The Zero trust network security emerged as a strategic and paradigm shift in the field of digital security. It follows a contrasting concept and removes trust within the organization's network architecture. It underscores the concept and approach of never trust, always verify. Hence, in this method, there is no trust within the inner network, and users or devices must always be verified. No one, whether an internal member or outsider, must not be trusted by default. In the Zero Trust approach, no one is entitled the benefit of the doubt and every user whether from inside or outside must prove their legitimacy before accessing to any of the organization's network resources.
Here in this method, organizations follow a strict access control regulations regardless of the network and location of the users.
The key features of Zero Trust Network Security includes:
Explicit Verification: In a Zero Trust Approach, every user or device trying to access the organization's resources and network must go through levels of authentication and authorization, regardless of whether an insider or outsider.
Principle of Least Privilege: The Zero trust approach is based on the principle of least privilege to restrict and limit user access, aimed at mitigating potential damage in the event of a security breach occurring.
Micro-Segmentation: The networks in the Zero Trust Approach are segmented into smaller and secure zones. This method is adopted to restrict and limit the lateral movement of threats. Each segment is powered with its own security policies and user access control.
Continuous Monitoring: In Zero trust network security, every activity and behaviour of the device and users are monitored continuously to ensure effective detection and responding to potential attacks/threats in real-time.
Assumption of Breach: The Zero-Trust Approach is guided by the assumption of the presence of threats and attackers within the network and not from outside, entailing organizations to design security strategy accordingly.
Putting in place and executing a Zero-Trust network security involves an amalgamation of technologies, including IAM (Identity and Access Management), MFA (Multi-Factor Authentication), security analytics, encryption and network segmentation. Adopting this zero-trust security approach will enable organizations to effectively protect and secure their sensitive data, reduce the risk of attacks and data breaches, and attain higher efficiency and enhanced security.
Some Examples of Zero-Trust Network Security
Below are a few use cases and examples that employ Zero-Trust Security approach
Cloud Security: With organizations increasingly adopting cloud technology, ensuring stringent identity authentication and access has become more important. The Zero-Trust model provides an excellent measure for organizations to implement higher security and protection of cloud resources.
Data Centre Security: Zero-trust model enables organizations to implement strong security and protection of their sensitive data through secure segmentation of network security and controlling employing methods like device security posture, user authentication and other factors.
PAM (Privilege Access Management): With Zero-Trust model of network security, enterprises can manage and secure privilege accounts.
Partner and vendor Access: With the Zero-Trust model, enterprises can grant access to third parties securely without putting their security structure at risk, and enforcing the security controls and authentication protocols for internal users.
Security for remote work culture: Zero-trust models enables organizations to have a secure and protected remote work culture and allows securing of data access requests from diverse devices and locations.
Major differences between Traditional Security and Zero Trust Security
- Traditional security is dependent on network perimeter as trust boundary. Zero-Trust, on the other hand, invalidates the idea of a trusted internal network.
- In traditional security, users and devices are assumed to be trustworthy while zero-trust does not make any such assumption regardless of an inside or outsider, or any sources and location.
- Traditional security is based on network location, on the contrary Zero-Trust is based on authenticity of the device and identity and other contextual factors.
- Traditional security architecture is modelled on Castle-and-Moat approach, while Zero-Trust has a decentralized and micro-segmented network and access control.
- Attackers have free rein in case of data breach in traditional model while in Zero-trust even in the event of breach, close monitoring is maintained on the movements of the attackers
Traditional and Zero-trust models are both vital measures of security. However, in today’s advanced and highly sophisticated era of digital threat landscape, the Zero-trust model has become a vital instrument of cybersecurity.
Comparison: Traditional vs Zero Trust
Why Zero Trust Is Winning
Hybrid Work Is Here to Stay: 68% of businesses have embraced hybrid models. Employees require secure access to devices and locations.
Cloud Proliferation: Borders of traditional networks are eroding. Workloads go across AWS, Azure, GCP, SaaS platforms, and edge devices.
Insider and Credential Threats: More than 80% of the breaches contain compromised credentials or internal abuse (Verizon DBIR).
Regulatory Pressure: Governance like NIST 800-207, CISA Zero Trust Maturity Model, and GDPR requires least-privilege and data minimization.
In Traditional Security: An attacker gaining entry into one employee's VPN session might be able to access databases, file shares and key systems with little resistance. A password-stealing phishing attack may open broad access due to the absence of stepwise authentication. In Zero Trust: The same attacker is confronted with step-by-step authentication barriers—MFA, device verification, behavioural anomaly detection and microsegmentation. Even if a breach does take place, harm is contained by strong, scoped access and session timeouts Zero Trust Network Access (ZTNA) is a new paradigm in security that effectively defies the conventional "trust but verify" method of network access. Rather, it relies on the "never trust, always verify" policy. Irrespective of whether a user or a device is within or outside the corporate boundary, ZTNA does not presume implicit trust and demands ongoing authentication, authorization and context-driven validation before it allows access to a resource. Fundamentally, ZTNA mandates least privilege access, whereby users and devices have access to only the applications or data they are specifically approved to access. This granular, need-to-know basis minimizes the attack surface area and restricts lateral movement in the case of a break. Difference between ZTNA and ZTSM: Conventional models of security would generally depend on perimeter controls like firewalls and VPNs, which take it for granted that users within the company network are secure. After they're let in, users tend to have wide access to internal infrastructure—leaving the network exposed if credentials are lost or an insider turns malicious. ZTNA replaces this legacy model with identity- and context-driven access controls. Each access request is dynamically assessed against a range of criteria, including: User identity and role Device posture and health Geolocation and access time Authentication strength (e.g., MFA) Continuous risk assessments or behavioral anomalies Most ZTNA implementations include the following architectural components: Policy Enforcement Point (PEP): Intercepts user requests and applies security policies. Policy Decision Point (PDP): Decides access based on identity, context and policy rules. Identity Provider (IdP): Verifies and authenticates user credentials. Trust Broker or Controller: Serves as the focal point of access logic, frequently relying on machine learning and risk scores. ZTNA may be integrated with current Identity and Access Management (IAM) infrastructures and endpoint detection tools to provide dynamic, real-time access controls. There various types of ZTNA solutions currently available, frequently overlapping with larger cloud security architectures: 1. Secure Access Service Edge (SASE) ZTNA is a core element of the SASE design, which unifies networking and security capabilities in a cloud-native service. SASE combines ZTNA with SD-WAN, cloud firewalls, CASB (Cloud Access Security Broker) and threat intelligence—providing secure, policy-based access from anywhere. 2. Software-Defined Perimeter (SDP) SDP architectures establish dynamically provisioned, encrypted tunnels between users and targeted services without exposing internal infrastructure to discovery. Access is only granted after authenticating identity, device security posture and compliance verifications. This micro-segmentation by design blocks lateral movement. 3. Identity-Driven Access Control Systems These sites are based on user identity, utilizing contemporary authentication techniques including Single Sign-On (SSO) and Multi-Factor Authentication (MFA) to validate and authenticate each session. Sophisticated solutions utilize behavior analytics to identify abnormalities and dynamically revoke access if risk is detected. 1. Security for Remote Workforce ZTNA in Action: Remote workers have to undergo identity (SSO, MFA), device health (patches, AV, encryption), and context-based checks (location, anomalies) before accessing particular applications such as CRM. Access is session-based with continuous monitoring and real-time revocation when there is risk detection. Benefits: Restricts lateral movement Ensures compliance (e.g., HIPAA, GDPR) Keeps productivity secure 2. Third-Party Vendor Access ZTNA in Action: External vendors are granted limited role-based access to only the tools or files they need (e.g., invoicing app). Federated identity, just-in-time provisioning and microsegmentation prevent any exposure outside their purpose. Everything is logged and time-stamped. Advantages: Reduces third-party risk Enables rapid, secure onboarding/offboarding Facilitates compliance and auditability 3. Cloud & Multi-Cloud Security ZTNA in Action: ZTNA imposes consistent policies on public clouds (AWS, Azure, GCP), private data centers and SaaS. Identity-aware gateways enforce access policies by user context, not location, with cloud-native integration and workload segmentation. Benefits: Unified access control across environments Reduces misconfigurations and attack surface Secures digital transformation 4. Secure DevOps & CI/CD ZTNA in Action This is done only by approved DevOps users through JIT access and contextual policies to tools such as GitHub or Kubernetes. Access is closely scoped, integrated into CI/CD pipelines and is revoked after the task in order to limit exposure. Advantages: Secure code and environments Enforces least-privilege practices Balances security with agility 5. Mergers, Acquisitions & Partnerships ZTNA in Action: ZTNA enables secure collaboration under M&A by allowing policy-based access to shared infrastructure—without complete network integration. Both sides maintain control over infrastructure, while ongoing monitoring maintains compliance. Advantages: Accelerates integration Prevents inherited risks Permits secure cross-org collaborationReal-World Implications
What is Zero Trust Network Access (ZTNA)?
How ZTNA Is Different from Conventional Network Architectures
Core Elements and Architecture of ZTNA
Types of ZTNA Solutions
ZTNA in Action: Use Cases
Conclusion: ZTSM vs Conventional Security
Traditional perimeter-focused security relies on users within the network and is thus open to lateral threats and insider attacks. Zero Trust Security Models (ZTSM)—particularly via Zero Trust Network Access (ZTNA)—apply tight, context-based authentication to each request for access. This reduces exposure, applies least privilege and supports cloud-first, remote-first environments that dominate today. With threats changing so much, Zero Trust isn't a choice—it's a necessity for secure digital operations at scale.